CASTOR’s technologies will be validated through real-world use cases that involve sharing security and safety-critical information across various domains, such as connected cars, automated mobility, drones in Flying Ad-Hoc Networks, and airspace applications.
Use Case 1
Highly Available & Secure Airspace Monitoring in Urban Air Mobility (UAM) Environments (COLLINS and ORO)
Airspace monitoring has gained significant attention in the aviation transport system, particularly with the emergence of new operational modes like small electric aircraft that can take off and land vertically at designated vertiports. This shift necessitates enhanced data monitoring and exchange to ensure the safe operation and coordination of these vehicles. Critical to this process are robust airport monitoring and detect-and-avoid systems that prioritize security while transmitting vital airspace data, such as speed and air traffic. To support on-ground airport personnel effectively, data communication links must offer high security, integrity, availability, and reliability.
The first use case aims to validate the CASTOR framework for establishing trusted paths across both intra- and inter-domain environments. It will address key challenges, like:
- ensuring continuous authentication for all devices to support secure and reliable data sharing services;
- consistently assessing the trust levels of software and hardware infrastructure elements and abstracting this information to evaluate the overall trust state;
- establishing or reconfiguring trusted paths with high reliability without disrupting service continuity;
- minimizing maintenance costs while reducing network disruption.
By enabling a safe, adaptable, and enforceable secure service through cloud-based orchestration solutions that ensure data integrity and trustworthiness, this use case aims to create a robust “below-the-radar” solution that can withstand attacks or faults, all while adhering to strict safety and security regulations such as EASA, CEN, ARINC 811, and EUROCAE.
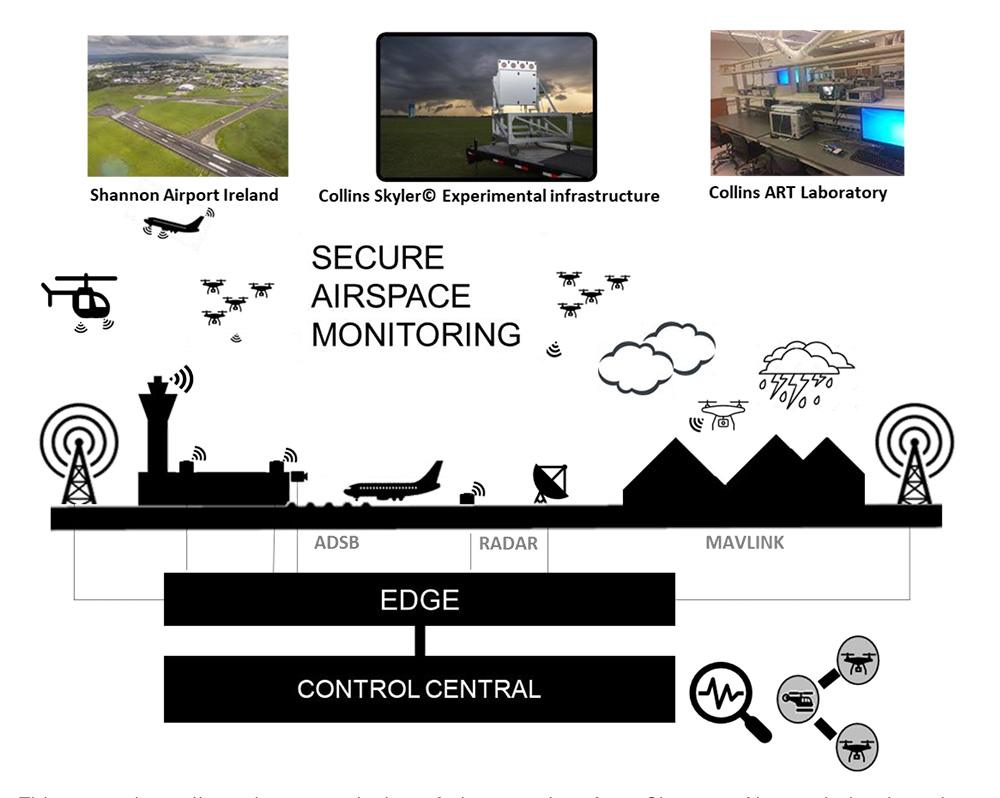
This scenario outlines the transmission of airspace data from Shannon Airport, Ireland, to the Collins Aerospace Laboratory in Cork. This setup features an in-network computing aggregation service that forwards data to a cloud-based service via a private 5G-enabled testbed comprising network elements. The airspace will be augmented with a fleet of simulated UAVs to explore a next-generation integrated monitoring framework for future aerial vehicles.
 This scenario extends the previous evaluation by examining communication between different administered domains, simulating two airports through testbeds in Ireland and Romania. The focus shifts from intra-domain to inter-domain endpoint path requirements, assessing CASTOR’s (FAD) capabilities in facilitating the negotiation and establishment of a trusted path configuration that maintains the confidentiality of domain-sensitive information for network operators.
This scenario extends the previous evaluation by examining communication between different administered domains, simulating two airports through testbeds in Ireland and Romania. The focus shifts from intra-domain to inter-domain endpoint path requirements, assessing CASTOR’s (FAD) capabilities in facilitating the negotiation and establishment of a trusted path configuration that maintains the confidentiality of domain-sensitive information for network operators.
In this setup, airspace-related data collected by the devices from both testbeds will be shared via an end-to-end path established with the trust extensions and governance features of CASTOR. Additionally, the devices will incorporate CASTOR’s SSI enhancements, including a secure version of the IDS Connector, to enforce access and usage control policies at the device level. This ensures that only authorized users can access transmitted data, enabling airspace monitoring vendors to maintain robust data control with increased automation.
Use Case 2
Trustworthy Communications of First Responder Mobile Units & the Compute Continuum (CMS, FERON, ORO)
First responders operate in safety-critical conditions. There is a need for secure and trusted collaboration among various units within traffic environments including third-party vehicles and Vulnerable Road Users (VRUs).
The use case combines the often-misinterpreted concepts of safety, security and trust in a single application and various communication scenarios. The specialty here is that in CASTOR we extend the concept of trusted path link through multiple technologies and networks. It connects client devices utilizing advanced high-demand CCAM scenarios and exemplifies secure mission-critical Vehicle-to-Everything (V2X) operations within unprotected mobile network environments, fostering trust between first responder mobile units operated by various authorities under various policy domains and the infrastructure. Itdemonstrates the creation of resilient and trusted communication paths characterized by low latency and high message integrity.

First responder vehicles (e.g., light vehicles like police motorbikes) enhance situational awareness by continuously sending Vehicle-to-Vehicle (V2V) awareness messages (i.e., Cooperative Awareness Messages, CAMs and DENMs) to surrounding vehicles. The scenarios use special OBUs, a compact, lightweight, on-board V2X communication station targeting micromobility, that does not rely on extended OEM back-end systems, circumventing spatial limitations of cellular coverage. High-rate CAM messages from motorbikes are transmitted via ITS-G5 warning other vehicles on a collision course. In this use case, it is essential to protect communications among vehicles involved in the first responder operation by ensuring that the messages generated by the vehicles in the group are trustworthy and credible. This use case is particularly relevant in high-speed, high-risk scenarios where visibility is limited, and the chances for timely recognition of dangerous traffic situations are minimal.
Defining mechanisms to enable performance and trust between first responder’s mobile units and the compute continuum is a primordial goal of CASTOR while first responders may be operated under different policy regimes and governed by different authorities.
One element of trustworthy communication is to obtain certificates for secure communications from a trusted agent in a trustworthy way. The focus of this scenario is on the periodic communication between OBU-equipped vehicles and the backend Public Key Infrastructure (PKI) to issue short-term anonymous credentials (pseudonyms) for the secure and privacy-preserving exchange of Cooperative Awareness Messages (CAMs). Establishing resilient paths with low latency and high certificate integrity is crucial, as any compromise could impact safety and security. The compute continuum connects the OBU via WiFi or Bluetooth to a handheld device that provides backend access.
CASTOR will also explore the use of vendor-specific or third-party applications, which are expected to coexist on European roads based on consumer preferences for shared or owned bikes. Information exchange with the cloud-based PKI occurs through a regular 4G/5G link from the handheld application.
This scenario focuses on remote asset management and control of responders by transmitting special codes and commands and software/firmware updates from the backend in a V2N2V scenario. It looks to establish high-availability, resilient, and integrity-focused trustable communication paths. Additionally, it addresses performance by trustable slicing and safety routing and satisfies synchronization aspects (i.e., allowing the vehicle to request software/firmware updates using a specific sequence number). 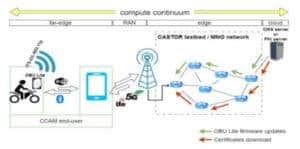
Use Case 3
Priority-based Trusted Messaging & Scalable Performance for CCAM Applications (ORO, TUIASI)
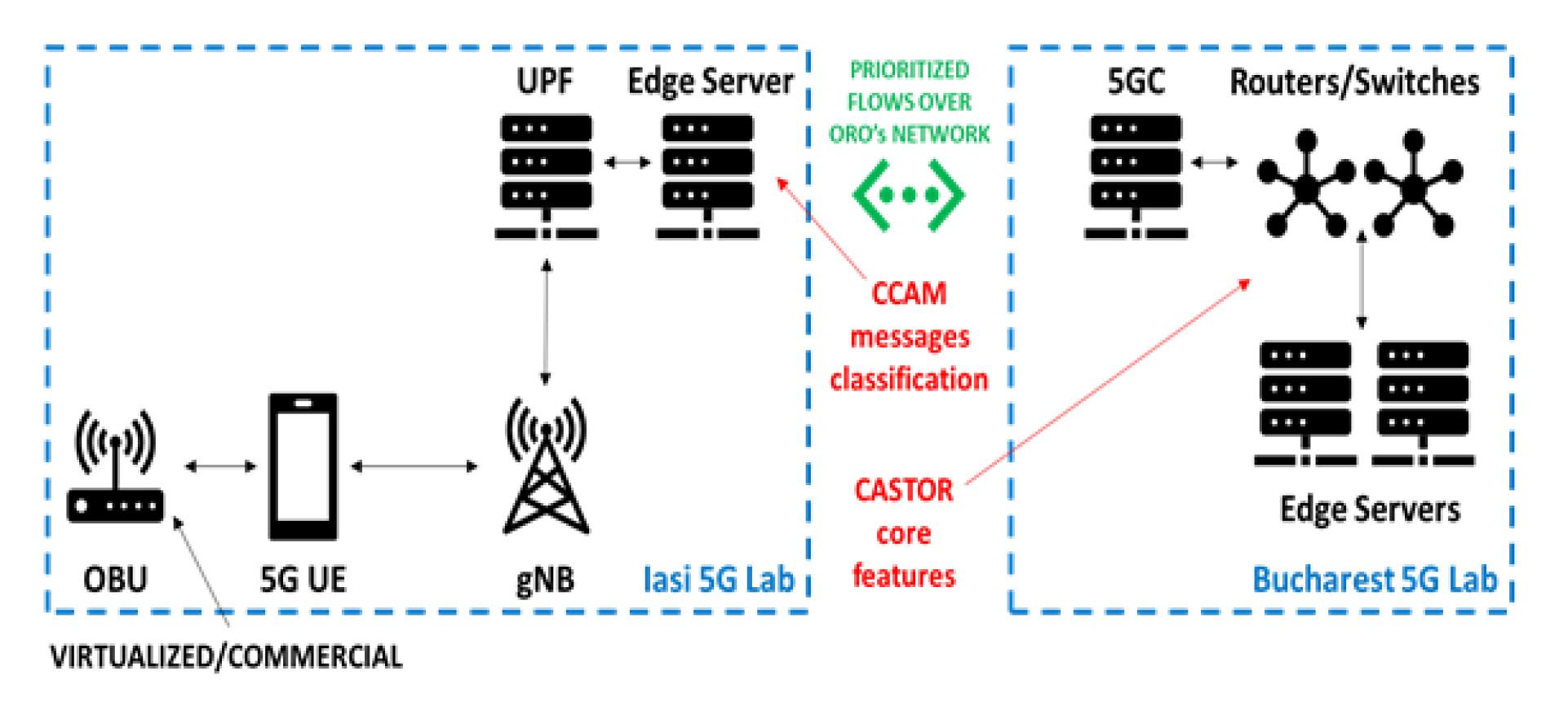
The third use case takes a broader perspective on Connected Cars and Automated Mobility (CCAM) functions, emphasizing the need for trusted communication paths to infrastructure and vice-versa. It also addresses diverse latency requirements shaped by trust assessment mechanisms, message priorities, and the increasing number of users.
A virtualized On-Board Unit (OBU) will be developed to simulate the generation of Cooperative Awareness Messages (CAM) and Decentralized Environmental Notification Messages (DENM), with DENMs given higher priority due to their critical nature. The messages generated by virtualized OBU will be transmitted via a real 5G network in which the CASTOR’s solution will reside.
Through this setup, the evaluation activities will analyze CASTOR’s capabilities on Connected Cars and Automated Mobility (CCAM) functions, analyses that are essential for demonstrating CASTOR’s applicability and fulfillment of trusted-path-routed services for critical applications.
The evaluation of CASTOR’s trusted-path establishment will focus on several dimensions that have not been thoroughly investigated in real-world field testing. These include the routing of messages with varying priorities, the scaling of users, and the effects of trust assessment mechanisms on end-to-end delay in relation to 5G 3GPP-defined requirements.
Use Case 4
Future-Proofing Next-Generation Unmanned Aerial Vehicles Communications towards Critical Infrastructure Sustainability (K3Y, ORO)
Background: The advancement of next-generation networks enables Unmanned Aerial Vehicles (UAVs) to inspect critical areas continuously and reliably. With the support of 5G and future networks, drones can create Flying Ad-Hoc Networks to execute cooperative missions and harness swarm intelligence through drone-to-drone communication.
However, this raises cybersecurity risks like data interception, tampering, and GPS spoofing, which can compromise the computing continuum. Additionally, malicious activities targeting edge and cloud services, including those provided by the 5G Core, can disrupt drone communications, leading to lost connections or delayed data transmission. Timely transmission is crucial for the success of drone missions, necessitating trust assessments throughout the entire infrastructure.
CASTOR brings a paradigm shift by enhancing SDN-facilitated orchestration capabilities with integrated security controls. This encompasses everything from the zero-touch onboarding and authentication of drones to control centers, to real-time maintenance and updates via secure and authenticated channels tailored for 5G’s adaptable topology, which presents new attack vectors. A key advantage of this approach is its preparedness feature, which proactively establishes redundant path configurations within the 5G Core and N4 interfaces, allowing for a seamless transition when an attack is detected that necessitates isolating affected network elements. This capability is also critical for inter-domain drone-to-drone communication, fostering trust between far-edge devices and the broader infrastructure. The system demonstrates the ability to consistently create available, resilient, and trusted communication paths while ensuring message integrity efficiently.
A fleet of drones will be deployed to inspect a large energy infrastructure. The drones receive instructions and mission parameters via the testbed 5G network. During the inspections, the drones collect data and transmit it for processing, which may involve coordinating among themselves to cover a wide area efficiently.
This scenario aims to evaluate CASTOR’s capacity to establish alternate trusted path configurations in response to various Packet Forwarding Control Protocol (PFCP) cyberattacks, including DoS attacks targeting session deletion, establishment, and modification. These attacks can manipulate session IDs at the SMF layer, affecting data flow routing in the 5G Core. CASTOR serves as a complementary security measure to AI-assisted intrusion detection techniques, focusing on isolating malicious components and activating redundant UPF (User Plane Function) pathways. This ensures continued communication among the drones and maintains secure data transmission, highlighting the importance of redundancy, reliability, and service continuity in such scenarios.
Similar to the previous scenario, this extends communication between distant drones. Two testbeds will be utilized to support this deployment topology. Each testbed will have its own 5G Core, enabling drones in one domain to exchange information and coordinate their actions with drones in the other domain. The primary objective of this scenario is to demonstrate how an attack on one 5G Core can affect the established paths at the other 5G Core, adapting to changes in the trust score of the end-to-end communication path.
